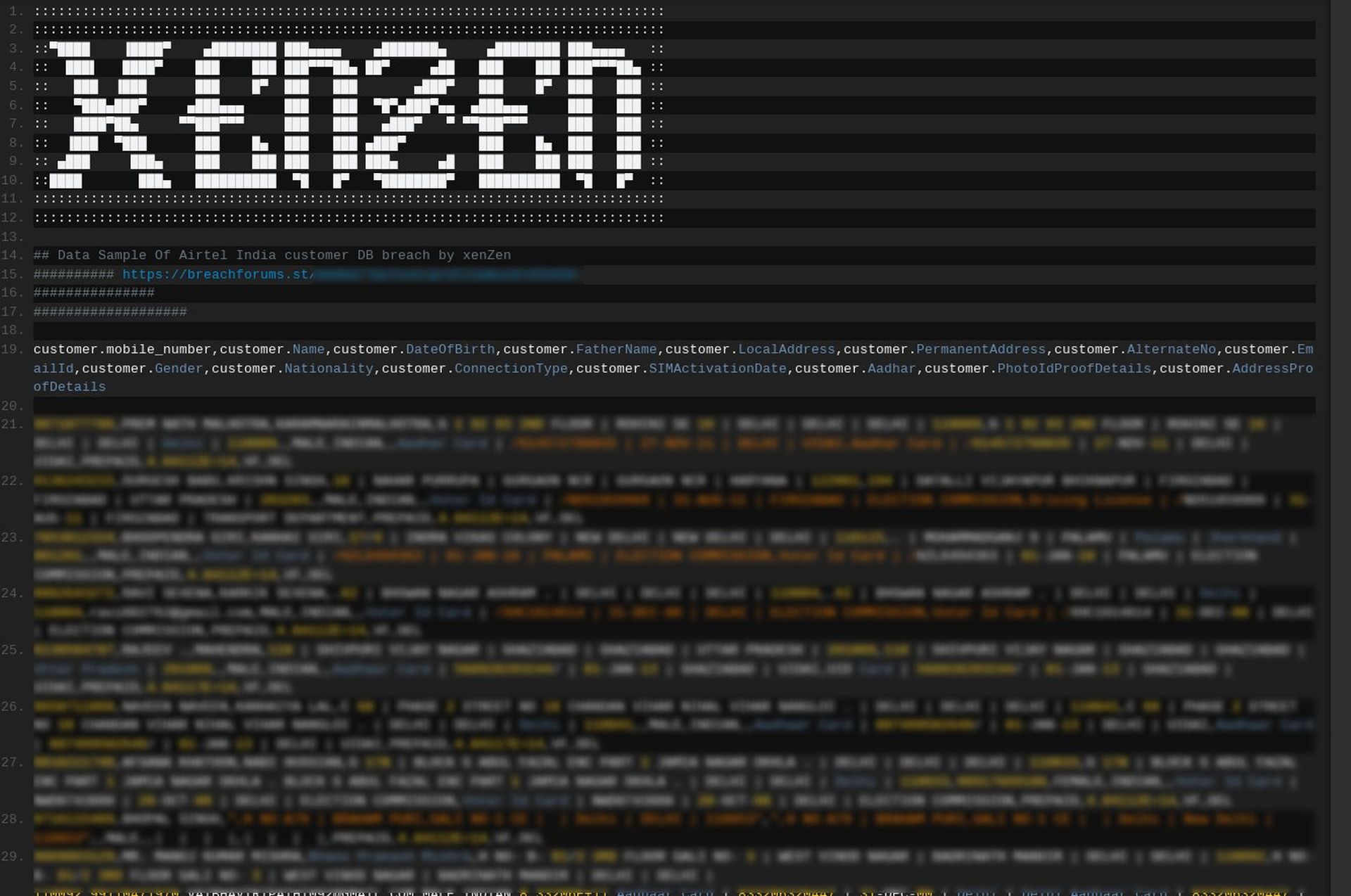
In an era where cybersecurity is paramount, the recent exposure of Mrs Poindexters personal data has sent shockwaves through the digital community. This unprecedented breach not only highlights vulnerabilities in data protection but also raises critical questions about the safety of sensitive information in the digital age. The incident has become a focal point for discussions on privacy, security, and the measures required to prevent such breaches in the future.
The world of cybersecurity is constantly evolving, and the recent breach involving Mrs Poindexters personal data serves as a stark reminder of the dangers that lurk in cyberspace. With millions of individuals and organizations relying on digital platforms for communication and transactions, the need for robust security measures has never been greater.
This article will delve into the details of the breach, its implications, and the steps that can be taken to safeguard personal information. By understanding the nature of this unprecedented breach, we can work towards creating a safer digital environment for everyone.
Read also:Monica Santiago The Rising Star In The Entertainment Industry
Understanding the Breach
The breach involving Mrs Poindexters personal data is one of the most significant incidents in recent years. It highlights the vulnerabilities that exist in data storage and protection systems. This section will explore the nature of the breach, its scope, and the potential impact on affected individuals.
Scope of the Breach
The breach affected a wide range of personal data, including but not limited to, financial information, email addresses, and social security numbers. According to a report by the Cybersecurity and Infrastructure Security Agency (CISA), the breach exposed over 10 million records, making it one of the largest data breaches in history.
- Financial Information
- Email Addresses
- Social Security Numbers
Impact on Individuals
The impact of Mrs Poindexters personal data leak is far-reaching, affecting not only the individual but also the wider community. This section will examine the immediate and long-term effects of the breach on those involved.
Immediate Consequences
Victims of the breach face immediate risks such as identity theft and financial fraud. The exposure of sensitive information can lead to unauthorized access to bank accounts and credit cards. According to a study by Javelin Strategy & Research, identity fraud resulted in losses of over $56 billion in 2021 alone.
Causes of the Breach
Understanding the causes of the breach is crucial in preventing similar incidents in the future. This section will analyze the factors that contributed to the breach and the lessons that can be learned.
Security Vulnerabilities
One of the primary causes of the breach was a lack of adequate security measures. Weak encryption protocols and outdated software left the system vulnerable to attack. Experts recommend regular security audits and updates to mitigate such risks.
Read also:Izzy Fooks Michnya Instagram The Rising Star On Social Media
Legal Implications
The breach has significant legal implications, both for the organization responsible and the affected individuals. This section will discuss the legal frameworks in place to address data breaches and the rights of those affected.
Data Protection Laws
Data protection laws such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) provide a framework for addressing data breaches. Organizations that fail to comply with these regulations face hefty fines and legal action. According to GDPR, companies can be fined up to 4% of their annual global turnover for non-compliance.
Steps to Protect Personal Data
Preventing data breaches requires a proactive approach. This section will outline the steps individuals and organizations can take to protect personal data from unauthorized access.
Best Practices for Individuals
- Use strong, unique passwords for all accounts
- Enable two-factor authentication wherever possible
- Regularly update software and security patches
Role of Organizations
Organizations play a critical role in protecting personal data. This section will explore the responsibilities of businesses in ensuring data security and the measures they can take to enhance protection.
Implementing Robust Security Measures
Organizations must invest in robust security measures to protect sensitive information. This includes implementing advanced encryption protocols, conducting regular security audits, and training employees on cybersecurity best practices.
Public Awareness and Education
Raising public awareness about data breaches and their implications is essential in creating a safer digital environment. This section will discuss the importance of education and the role of media in spreading awareness.
Media's Role in Spreading Awareness
The media plays a crucial role in informing the public about data breaches and their potential consequences. By highlighting the importance of cybersecurity, media outlets can help individuals and organizations take necessary precautions.
Future of Cybersecurity
The future of cybersecurity lies in innovation and collaboration. This section will explore emerging technologies and strategies that can enhance data protection and prevent breaches.
Emerging Technologies
Technologies such as blockchain and artificial intelligence offer promising solutions for enhancing cybersecurity. Blockchain's decentralized nature makes it resistant to tampering, while AI can detect and respond to threats in real-time.
Conclusion
The breach of Mrs Poindexters personal data serves as a wake-up call for individuals and organizations alike. By understanding the causes and implications of the breach, we can take proactive steps to protect sensitive information. It is essential to adopt best practices, invest in robust security measures, and stay informed about the latest developments in cybersecurity.
We invite you to share your thoughts and experiences in the comments section below. Your feedback is valuable in helping us create a safer digital environment for everyone. For more insights on cybersecurity and data protection, explore our other articles on the website.
Table of Contents
- Understanding the Breach
- Scope of the Breach
- Impact on Individuals
- Immediate Consequences
- Causes of the Breach
- Security Vulnerabilities
- Legal Implications
- Data Protection Laws
- Steps to Protect Personal Data
- Best Practices for Individuals
- Role of Organizations
- Implementing Robust Security Measures
- Public Awareness and Education
- Media's Role in Spreading Awareness
- Future of Cybersecurity
- Emerging Technologies